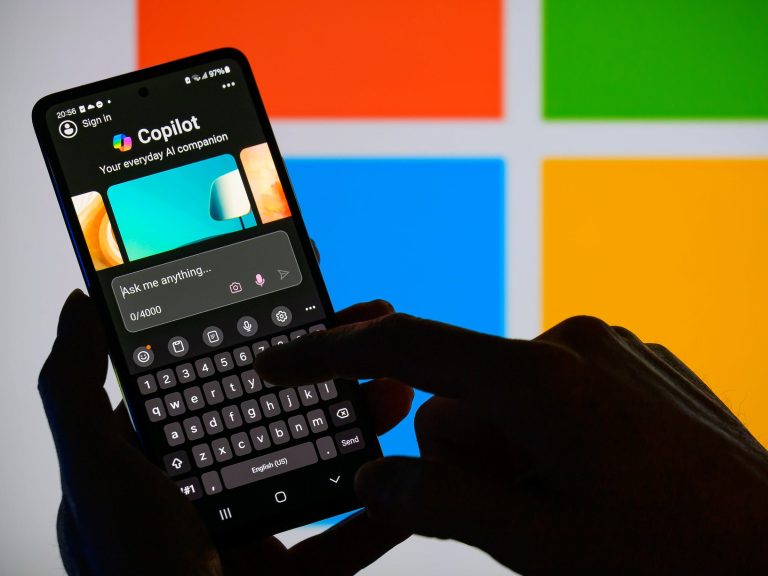
Microsoft’s AI Can Be Turned Into an Automated Phishing Machine Microsoft’s AI technology has the potential to be used in...
Security
How Infostealers Pillaged the World’s Passwords How Infostealers Pillaged the World’s Passwords Infostealers are malicious software that are designed to...
Inside the Dark World of Doxing for Profit Doxing, the practice of researching and publishing private or identifying information about...
Saboteurs Cut Internet Cables in Latest Disruption During Paris Olympics Saboteurs Cut Internet Cables in Latest Disruption During Paris Olympics...
A Senate Bill Would Radically Improve Voting Machine Security Recently, a Senate bill has been introduced that aims to enhance...
How Russia-Linked Malware Cut Heat to 600 Ukrainian Buildings in Deep Winter During the deep winter months in Ukraine, a...
An AWS Configuration Issue Could Expose Thousands of Web Apps Recent reports have surfaced about a potential AWS configuration issue...
Your Gym Locker May Be Hackable Your Gym Locker May Be Hackable When you hit the gym, you trust that...
Want to Win a Bike Race? Hack Your Rival’s Wireless Shifters Want to Win a Bike Race? Hack Your Rival’s...
A Hacker ‘Ghost’ Network Is Quietly Spreading Malware on GitHub Reports have surfaced about a hacker group known as 'Ghost'...