Apple Prototypes and Corporate Secrets Are for Sale Online—If You Know Where to Look In a shocking development, it has...
Security
'Sinkclose' Flaw in Hundreds of Millions of AMD Chips Allows Deep, Virtually Unfixable Infections A newly discovered flaw in hundreds...
Can GPT-4o Be Trusted With Your Private Data? As technology continues to advance, the use of artificial intelligence (AI) has...
Tricky Web Timing Attacks Are Getting Easier to Use—and Abuse Web timing attacks are a type of security vulnerability that...
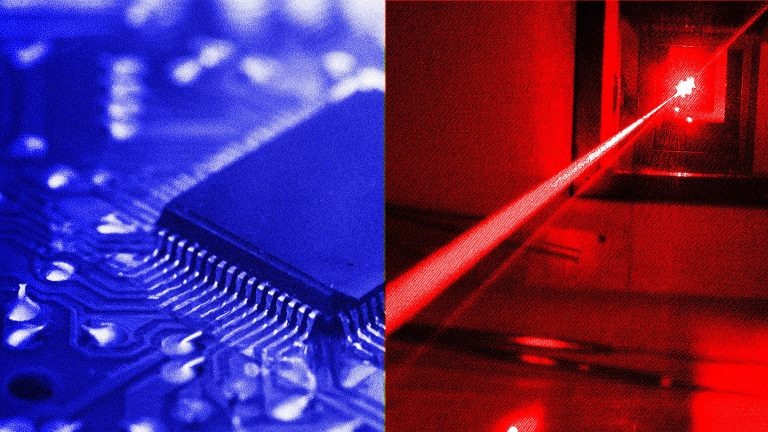
Watch How a Hacker’s Infrared Laser Can Spy on Your Laptop’s Keystrokes Imagine sitting at a cafe, typing away on...
How Hackers Extracted the ‘Keys to the Kingdom’ to Clone HID Keycards How Hackers Extracted the ‘Keys to the Kingdom’...
The Slow-Burn Nightmare of the National Public Data Breach In recent years, the threat of data breaches has become a...
A $500 Open Source Tool Lets Anyone Hack Computer Chips With Lasers Computer chips are the brains of modern technology,...
At the Olympics, AI Is Watching You As athletes from around the world compete in the Olympics, they are not...
USPS Text Scammers Duped His Wife, So He Hacked Their Operation USPS Text Scammers Duped His Wife, So He Hacked...